Protect your organization with intelligence to act before attackers do.
Monitor external threats on the public internet and dark web.
Organizations struggle staying ahead of external security threats.
When oblivious to threat intelligence, organizations overlook weaknesses and respond poorly to attacks. They are unaware of information that attackers use to exploit them and their customers. Leaders work reactively instead of proactively to manage risk and mitigate external threats to data. To make matters worse, building a threat intelligence program from scratch is challenging and right-sized solutions are hard to find. This creates opportunities for threat actors.
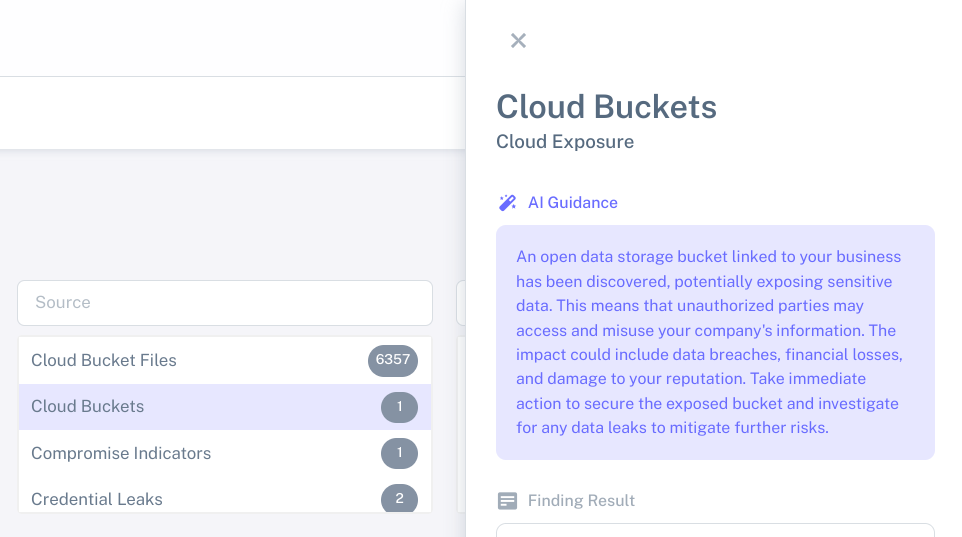
Cyber threat monitoring built to be within reach.
ThreatHarvest simplifies the process of developing and maintaining a threat intelligence program. Organizations set their information requirements while ThreatHarvest automates the ongoing sourcing, collection, and processing of data. This results in organizations staying informed and able to take action to protect themselves.
- Know what makes you attractive to an attacker
- Understand emerging threats and risk indicators
- Protect what matters the most to your organization
Advanced threat intelligence for any organization.
Savvy leaders look beyond their network for threat information to understand their weaknesses. However, the threat intelligence marketplace can be focused on the needs and budgets of large enterprises. ThreatHarvest is designed to fit any organization, including small and medium businesses.
Features & Benefits
- Implement a threat intelligence program based on specific requirements
- Monitor for any new information related to each information requirement
- Perform reconnaissance like an attacker, with no disruptive active scans
- Configure notification emails that summarize new findings when available
- Make threat intelligence possible even without a dedicated security team
- Contextualize findings using an artificial intelligence virtual assistant
Results & Objectives
- Know when to take steps to protect assets, data, and brand reputation
- Stay informed of infrastructure a bad actor may have deployed for a future attack
- Identify unintended consequences resulting from changes to systems
- Uncover sensitive information that has leaked or is being unintentionally exposed
- Detect impacts of shadow IT, and the addition of unexpected systems or services
- Discover conditions that are highly attractive to threat actors
Plus emerging feeds, social platforms, and more!
Cyber threat monitoring built to be simple.
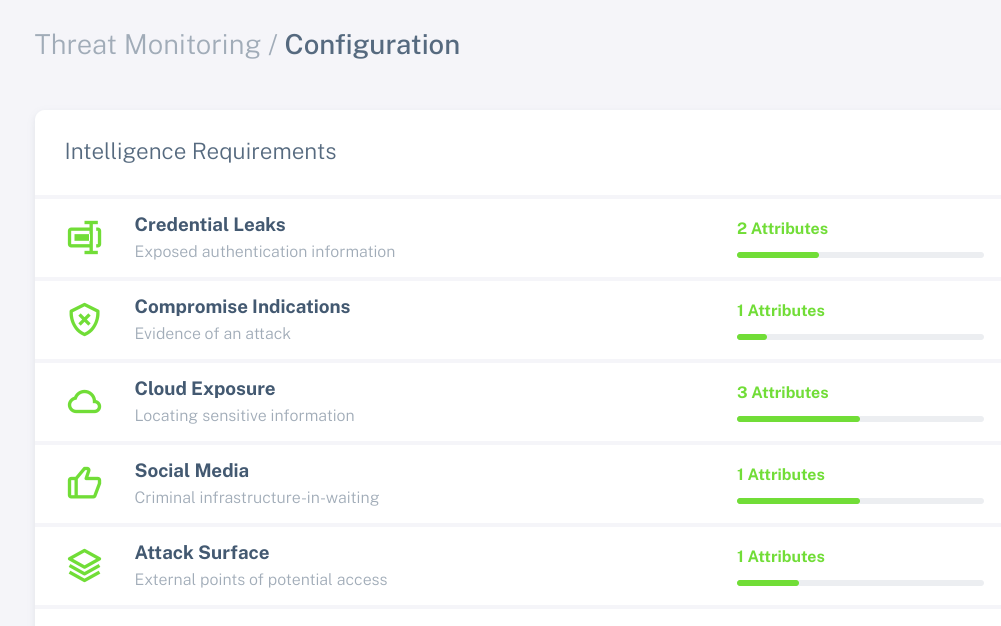
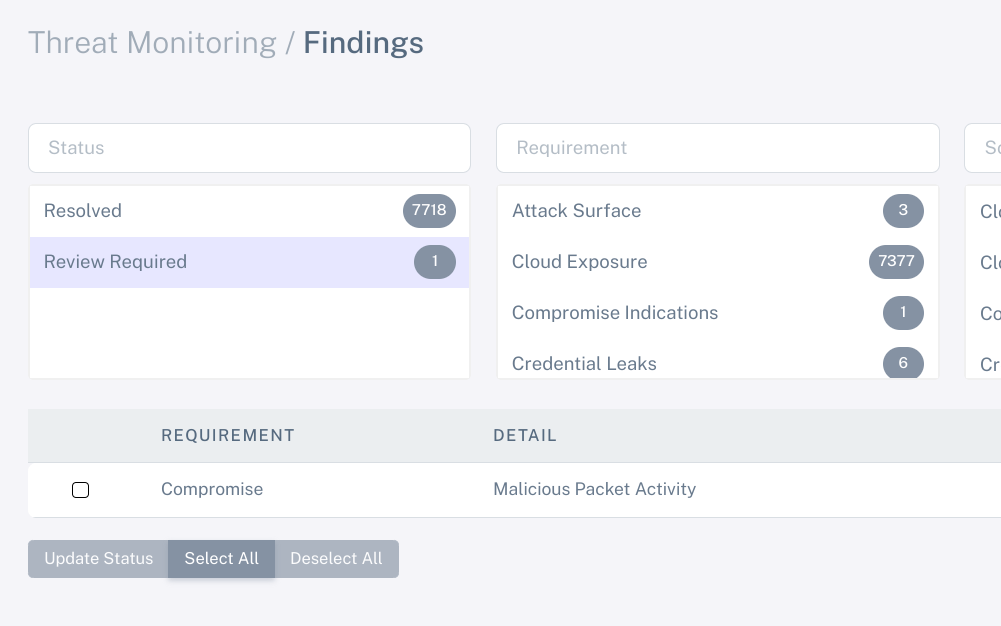
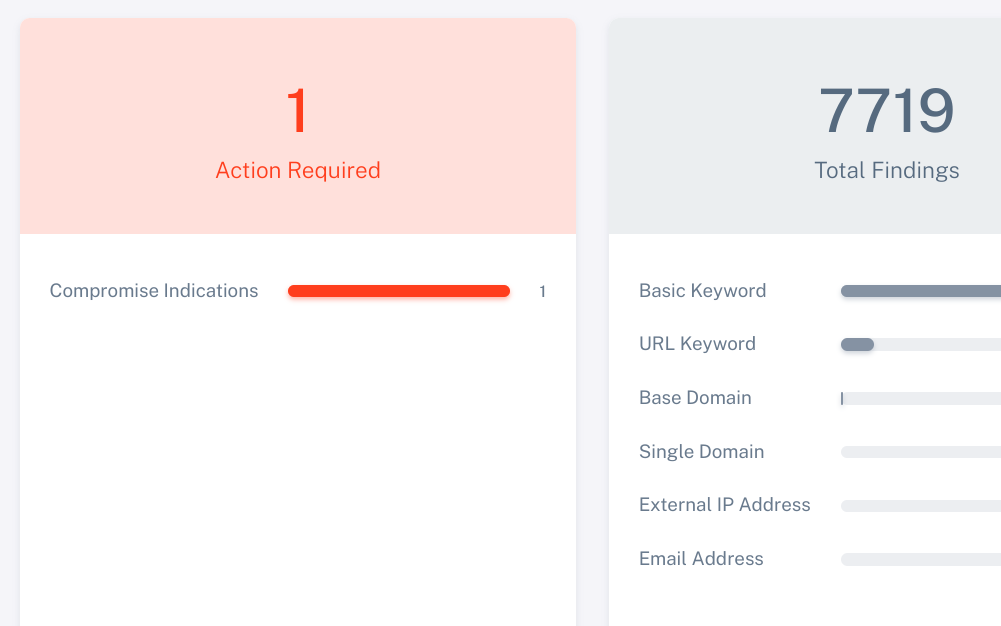
Threat monitoring tools should balance risk reduction and cost.
Threat intelligence should not be limited to the budgets of large enterprises.
Starter
Ideal for startups and small teams
99
/month- Threat Monitoring
- AI-Enabled Guidance
- Email Notifications
HOVER FOR
MORE DETAIL
Standard
Perfect for growing businesses
179
/month- Threat Monitoring
- AI-Enabled Guidance
- Email Notifications
HOVER FOR
MORE DETAIL
Premium
Best for expanding coverage
329
/month- Threat Monitoring
- AI-Enabled Guidance
- Email Notifications
HOVER FOR
MORE DETAIL
Drop us a note if you have specific requirements that you’d like to talk about.
Getting started is easy!
1
Subscribe
Get immediate access to cyber threat monitoring services
2
Set Requirements
We help establish your custom threat intelligence program
3
Stay Informed
We monitor external cyber threats and alert you when found
Still have a question?
Feel free to browse answers to commonly asked questions below.
